For a security team looking to add new tools to their organization it can be challenging to sort through floods of repetitive marketing to find the capabilities you actually need.
In this blog post we break down common cybersecurity tool categories and how the need for a unified Security Operations (SecOps) platform led us to create Kaleidoscope.
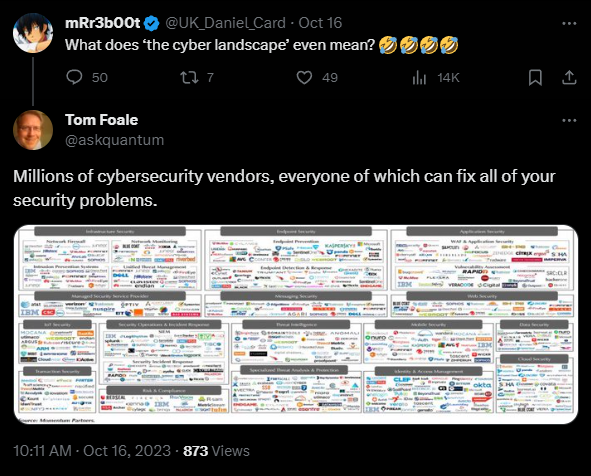
Cybersecurity as an industry has evolved drastically over the last two decades, from applying a perspective and skillset in IT operations to a thriving ecosystem and business vertical of its own. From the early days of Anti-virus and firewalls to today’s expensive landscape of corporate networks and million-dollar tools, we’ve seen a slew of products manifest to solve the various problems that arise in applying security controls and policies to corporate networks. Cybersecurity tooling has continued to evolve into more holistic and comprehensive coverage of the assets and networks that keep businesses running to keep up with the threats they face. With this expansion of products has come a saga of branding and marketing adjustments to differentiate products from one another and demonstrate the problems they’re solving. This process of categorization provides businesses with the tools they need to market their product to their end users, and for potential customers to identify the needs and budgets to which they align.
For the cybersecurity generalist and less sophisticated enterprises, this stratification forces them to decipher a mountain of buzzword-like product names to determine which tools to prioritize and purchase and how they apply to the existing processes their security organizations go through. It can be challenging to figure out what each of these product categories mean in isolation and how they can be tied together as part of a holistic cybersecurity strategy. As a product company, Outcome Security has had to apply a discerning eye to these categories to identify relevant candidates for integration, as well as the branding required to both differentiate and normalize the position of Kaleidoscope in the wider ecosystem. As part of this effort, we’ve identified some of the current trendy product categories and will seek to identify them uniquely as well as what they bring to the table. This listing of categories is only the beginning of the broad spectrum that might be considered the cyber landscape but are chosen here as most tangentially relevant to the efforts we focus on at Outcome.
*DR (EDR, XDR, MDR, NDR)- Detection and Response
Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), and Managed Detection and Response are endpoint-focused tools for gathering telemetry, monitoring machines, and handling the follow-up on alerts associated with host-based indicators of compromise (IOCs). EDR acted as an evolution on the standard endpoint-deployed AV, performing the core function of managing individual endpoint systems and shipping telemetry back to a central source. Network Detection and Response (NDR) is the network-focused equivalent to the prior products. Rather than handling host-based indicators, NDR focuses on network traffic, and data like domains, IPs, and similar. XDR iterated on the EDR formula further by acting to consolidate additional distinct sources of information to include network and cloud assets, identity, and email. Meanwhile, MDR hands some of the reigns of an organization’s security operations over to an external third party that acts as a SecOps team at scale for its customers.
TIP – Threat Intelligence Platform
Threat intelligence platforms are designed to source, aggregate, and deconflict threat intelligence data. Generally, threat intelligence data includes “known bad” IOCs and attribution to threat actors associated with ongoing external malicious activity that organizations can use either to hunt within their environment or to help prioritize existing incidents and alerts. Depending on the implementation and integration of the platform, a TIP may pull data into unified views, route the data to other systems, provide a feed of threat data to engineers and analysts, and prioritize and curate the data from disparate sources to assist in consuming the data.
SIEM – Security Information and Event Management
The goal of a SIEM is to gather information from a business’ assets and provide alerting and event tracking across the enterprise for SOC analysts and investigators. SIEMs characteristically focus on the collection of various logs, as centralizing logging is a practical and effective way to provide a holistic view across an enterprise and enable initial triage and alerting to analysts. SIEMs will not usually involve direct actioning of incidents, or deeper filesystem/host-based artifacts of an attack.
SOAR – Security Orchestration Automation & Response
Security Orchestration, Automation, and Response tools are most often used to action policies and deployments, and automate common security processes. Broken out into its component parts, orchestration will gather the data for actioning as part of an alert, automation will engage the relevant analysis and transformation of the data up to and including some deployment mechanisms like pushing policies or signatures to the network, and response describes that actioning arm.
IAM – Identity and Access Management
Identity and access management tools cover the collection of tools most commonly highlighted today through Zero Trust and similar efforts. These tools help manage, deploy, and monitor things like unified user information, credentials, and access privileges across the enterprise. They can be used to keep this highly sensitive information in an encrypted and manageable format as well as allow for wider policy configurations across distinct assets.
Asset Management
Many businesses have begun to utilize asset management utilities to track all assets across their infrastructure landscape. These tools bring together inventory management of various IT systems alongside risk scoring and risk association, and sometimes interdependency identification, to help provide a comprehensive understanding of what kind of vulnerabilities might be prevalent across the enterprise.
Others!
There are a myriad of additional categories of product that could be potentially relevant to cybersecurity processes and organizations: Case Management utilities, Data Loss Prevention, Cyber Insurance, are all examples of other tools that a cyber security organization may acquire or touch as part of their daily duties protecting the enterprise. In the modern cybersecurity landscape, many of these products overlap and blend into each other as they try to expand the scope of problems that they can solve. But rather than finding one product that solves all of their problems, many organizations end up with many products that their security teams need to coordinate between for different problems. For most teams, this means analysts open 15 browser tabs and handle their own note taking only to then relegate portions of it to emails, reports and tickets.
To mitigate the data leakage associated with this practice and take a more effective tact to handling posture and incidents within an enterprise, the industry has begun to implement a new, more holistic category of product referred to as a Security Operations (SecOps) Platform. This centralization of data and tooling can make a drastic difference in the effectiveness and efficiency of practitioners as they look to remediate and handle incidents no matter what systems have been infected along the way.
Outcome Security created Kaleidoscope to help analysts navigate this shifting, fractured landscape, and to help unify these disparate tools into a unified process.
Finding a Better Path
When we built Kaleidoscope, we sought to focus on solving a problem (detangling the web of cybersecurity data and tools to build a better foundation to collaborate on cybersecurity analysis) rather than building it into a category. Whatever the use case at hand, we wanted it to function as a central location for working with the data cybersecurity practitioners need to have a comprehensive and holistic approach. Kaleidoscope enables practitioners to work directly with log data from disparate sources and enrich their contents like a SIEM. It allows for automation of common processes into workflows to make its users faster and more efficient in utilizing that data. It normalizes and transforms data from a variety of threat intelligence providers and OSINT threat data, like a TIP. It can also track and enable case management functions common amongst project management and similar tooling to retain context around the actions users are performing. A little bit SOAR, a little bit SIEM, a little bit TIP, we’ve opted to call Kaleidoscope a Security Operations Platform.
Security operations covers a broad spectrum of use cases typically actioned by an organization SOC, from triaging alerts and phishing attempts, to handling the acquisition, deployment, and integration of new tooling and capabilities. A SecOps Platform provides an effective framework to evolve and develop a security team’s tool suite and processes, and maintain a unified perspective on the security posture of the organization overall. Kaleidoscope codifies this process of consolidation by focusing on and defining what functional building blocks different tools, data feeds, and integrations, provide to your security organization.
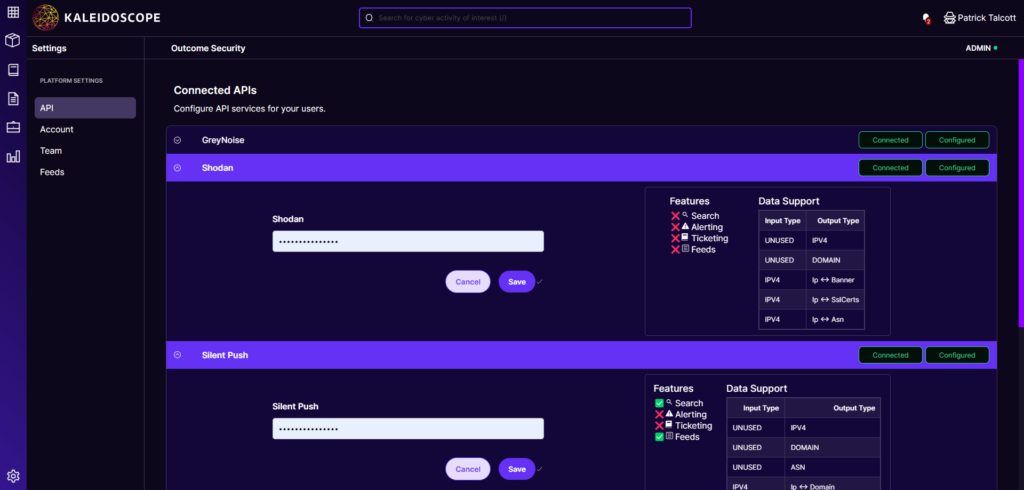
With the Security Operations team in mind, Kaleidoscope can act as the go-to source for all information across the various tools in place and inform the team to gaps in their existing tooling and operations for process improvement. Analysts can pick up individual security incidents and pull from all tools they use, no matter the category, as they become relevant to an individual investigation. They can use native tooling within the platform to deconflict this data, acquire additional context, and make new associations and analytical judgements about that data. When all is said and done it can act as a central repository of the unique analytical perspectives and findings of the organization and it can persist as a living breathing entity, ready and waiting to be applied to the next. Meanwhile this in-depth perspective can enable follow on automation of the repetitive processes that may cross from one product category to another and extend the functionality of these products in more synergistic ways. The leaders within the business can then receive key insights on the performance and processes employed in operations to understand their current security posture and where it can be most readily improved.